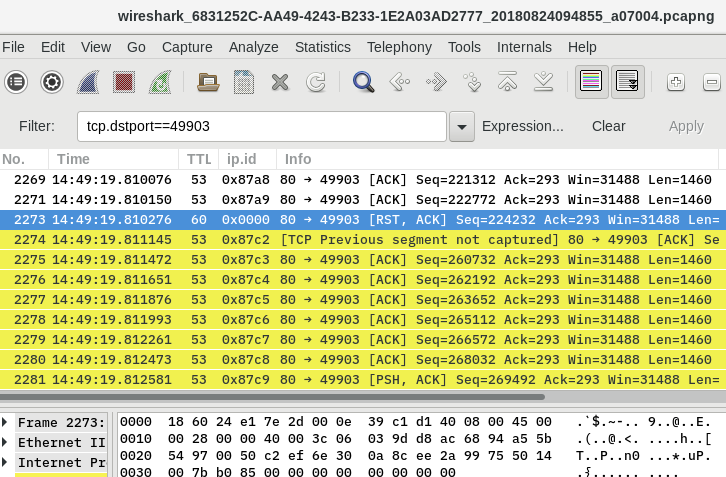
RST,ACK sent from server during file transfer
I'm attempting to troubleshoot a RentMaster program failing to update. Full disclosure I've had a class in college that had a wireshark exercise but not much experience beyond that. I've been poring over a capture session I took of the update itself and it appears to be caused by an RST,ACK packet sent with the source IP of the server (No. 2273). I've been doing some research and found that despite the source IP being the server, this RST may not be coming from the server itself but from another device along the route.
The TTL of the RST packet is 60 whereas all the download packets in the TCP stream before this were TTL=53. I believe, from the answers on this question, that this means it did not come from the server.
Capture Session. Again, I'm not especially experienced in Wireshark but would love it if anyone could help me verify or refute this theory. In addition, could the difference in the TTL be a way of identifying the culprit? Could I, for instance, trace the route from the host machine to the server and count the hops to figure out which device is preventing this download?


Comments